Administration
IAMS provides a set of APIs to manage the identity and access control.
IAMS also provides a Web Administration Console called IAMS-Web to allow you to perform the administration task via a Web UI.
You can use the IAMS-Web container image as-is, or customize the UI to suite your project needs. The source code to the IAMS-Web can be
found in the IAMS-Web Release Page
IAMS-Web uses the APIs to handle the administration tasks.
The concept explained below will apply to both APIs and IAMS-Web.
Each realm has 2 default system roles:
- system-admin
- tenant-admin
Users will system-admin role can perform all administrative tasks within the realm while user with tenant-admin role can only perform administrative tasks pertaining to the tenant that he is assigned administer to.
User must be a member of a tenant in order to be assign with tenant-admin role for that tenant. User can be a member of multiple tenants and hence, tenant-admin of multiple tenant.
IAMS provides APIs to allow management of the followings:
- User
- Tenant
- Role
- Group
- Resource
- Scope
- Permission
Please refer to the API documentation for more information.
you will need read access to AGIL Ops Hub private repository to download the API documentation.
If you have deployed IAMS locally, you can also access the APIs via to following link:
http://iams-aas.127.0.0.1.nip.io/swagger-ui/index.html
The following table document what user with system-admin and tenant-admin roles can invoke:
| Administration Tasks | system-admin | tenant-admin |
| User Management | ||
| List user | ✔️ | ✔️ |
| Create user | ✔️ | |
| Delete user | ✔️ | |
| Update user | ✔️ | |
| Get user | ✔️ | ✔️ |
| Tenant Management | ||
| List tenants | ✔️ | ✔️ Only return tenants that he is administrator to. |
| Create tenant | ✔️ | |
| Create tenant | ✔️ | ✔️ Only return tenants that he is administrator to. |
| Delete Tenant | ✔️ | ✔️ Only return tenants that he is administrator to. |
| Get tenant | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Tenant Memberships Management | ||
| List member of a tenant | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Add user as member to tenant | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Remove user from tenant | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List memberships of user | ✔️ | |
| List user not member of tenant | ✔️ | ✔️ Only can access tenant he is administrator to. |
| System Administrator Management | ||
| Assign user with system-admin role | ✔️ | |
| Un-assign user with system-admin role | ✔️ | |
| List user with system-admin role. | ✔️ | |
| Tenant Administrator Management | ||
| List all user with tenant-admin role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Assign user as tenant-admin | ✔️ | ✔️ Only can access tenant he is administrator to. The assignee need to be member of the tenant. |
| Un-assign user as tenant-admin | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Tenant Group Management | ||
| List top level tenant groups | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Create top-level tenant group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List subgroup from a group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Create subgroup to a group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Get group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Delete group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Add user to group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Remove user from group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List users in group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List groups user is in | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List roles assigned to group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Assign role to group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Un-assign role from group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List roles that can be assign to group | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Tenant Role Management | ||
| List roles in tenant | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Create a role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Delete role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List user assigned with a role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Assign users with a role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Un-assign users from a role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List of users that can be assigned with role | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List roles assigned to user | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Assign roles to user | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Un-assign roles from user | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List roles that can be assigned to user | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Tenant Scope Management | ||
| List all scopes | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Create a scope | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Delete scope | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Update scope | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List resources with scope | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Tenant Resource Management | ||
| List all resources | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Create resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Get resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Update resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Delete resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Add scope to resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Remove scope from resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List all resource scopes | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Tenant Resource Permissions | ||
| List all users granted scoped access to a resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Grant users with a scoped access to a resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List all roles granted scoped access to a resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Grant roles with a scoped access to a resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| List all groups granted scoped access to a resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
| Grant groups with a scoped access to a resource | ✔️ | ✔️ Only can access tenant he is administrator to. |
Set up User Account
Some modules require the user account to be assigned to a tenant, so you'll need to configure certain settings accordingly.
Create a New User Account
If you're already have an account but haven't assigned tenant for it yet go to this section
-
Open browser and access the
IAMS-Web. -
Login to the
IAMS-WEBwith an account that has theAdd Userpermission. -
After login you will be redirect to the Manage Users page, if not click on the
Manage Usersmenu item in the side menu.
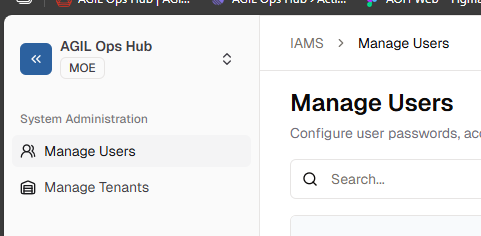
- Next, Click on
Create Userbutton.
- In the
Create Userform, enter the followings:
- Username – the desired username of the account. In the example below, myadmin is used.
- (Optional) Password - the desired password for the account.
For more information about password policies. Go to this section
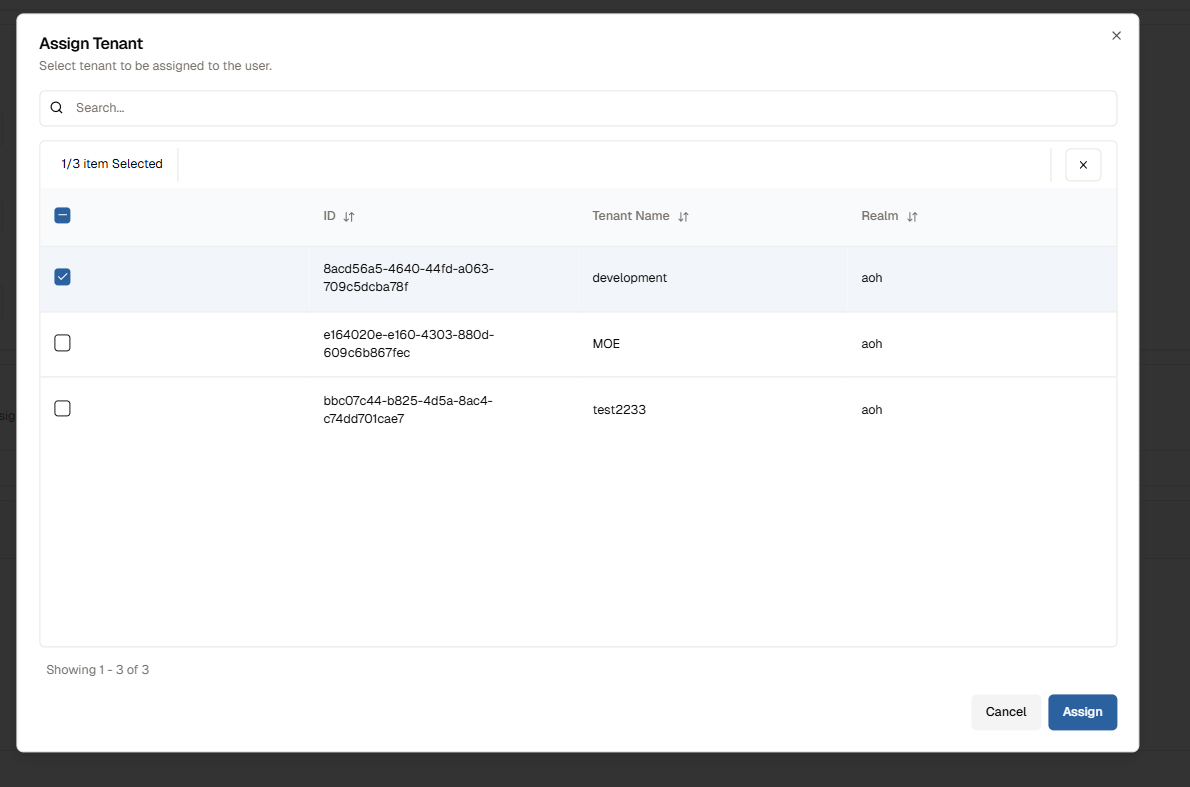
- Scroll down and click on
Assign Tenantbutton to open to theAssign Tenantdialog.
- Select tenants you want to assigned to the account and click "Assign" button. In the example below
developmentis used.
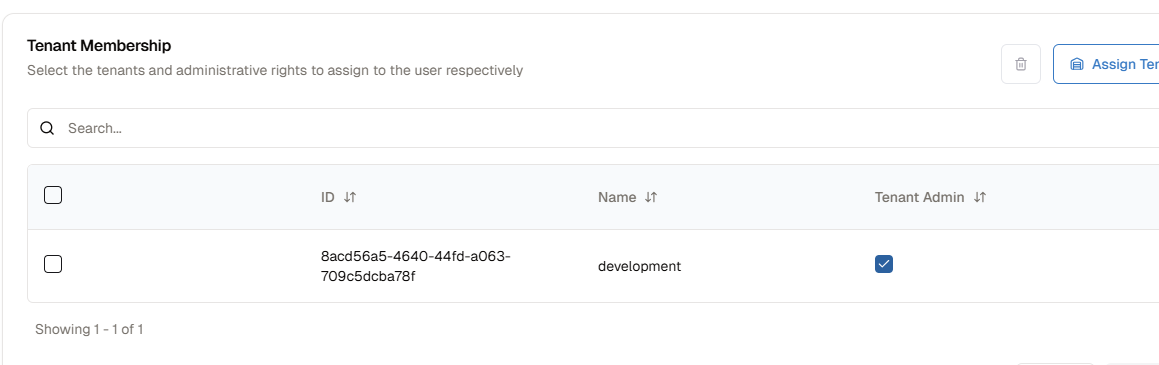
- (Optional) Check the
Tenant Adminoption in the Tenant Admin column if you want to setTenant Adminrole for the account.
- Click
Completebutton.
Assign the User Account to a Tenant
In case you want to assign an existing account to a tenant.
-
Open browser and access the
IAMS-Web. -
Login to the
IAMS-WEBwith an account that has theAdd to Tenantpermission. -
After login, click on the
Tenantsmenu item in the side menu.
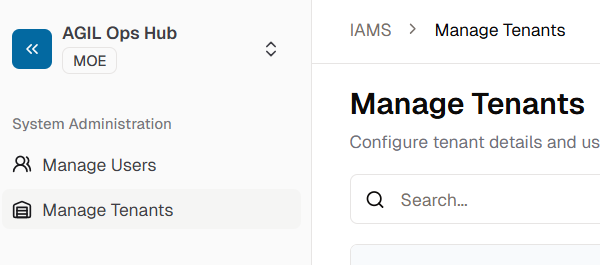
- Click on the tenant you want.
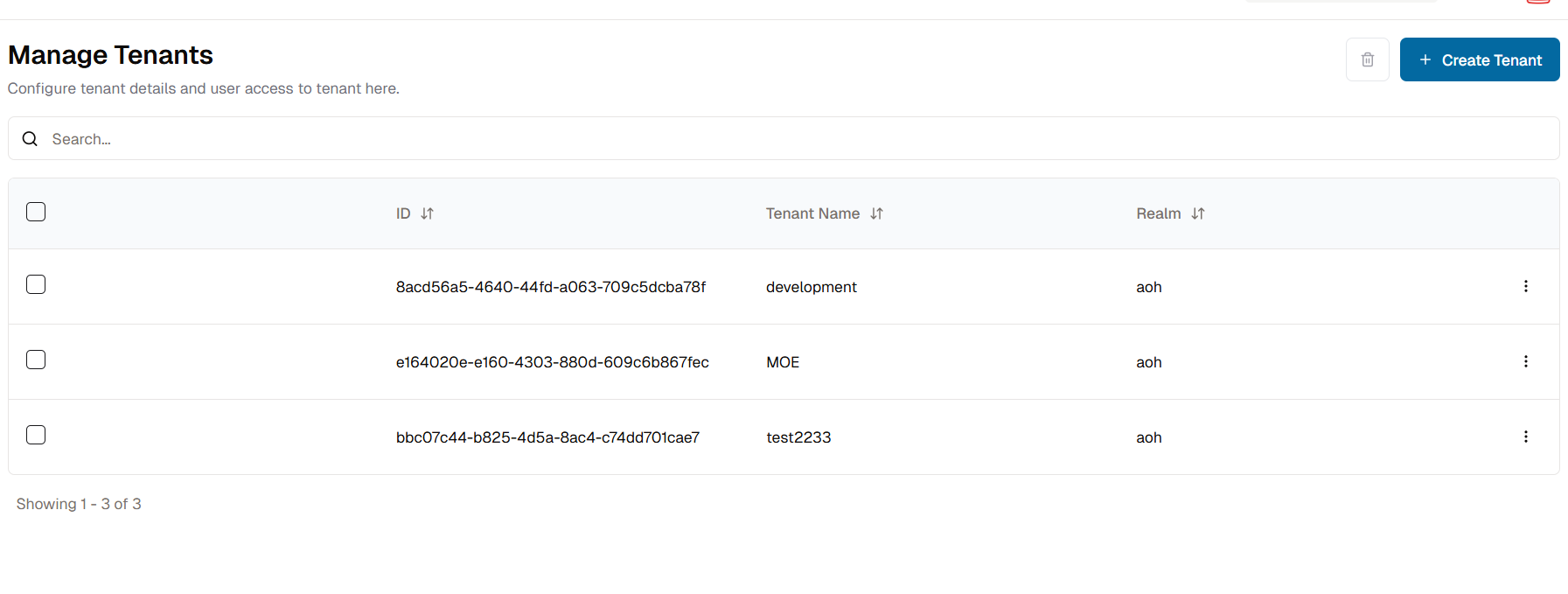
- Click on
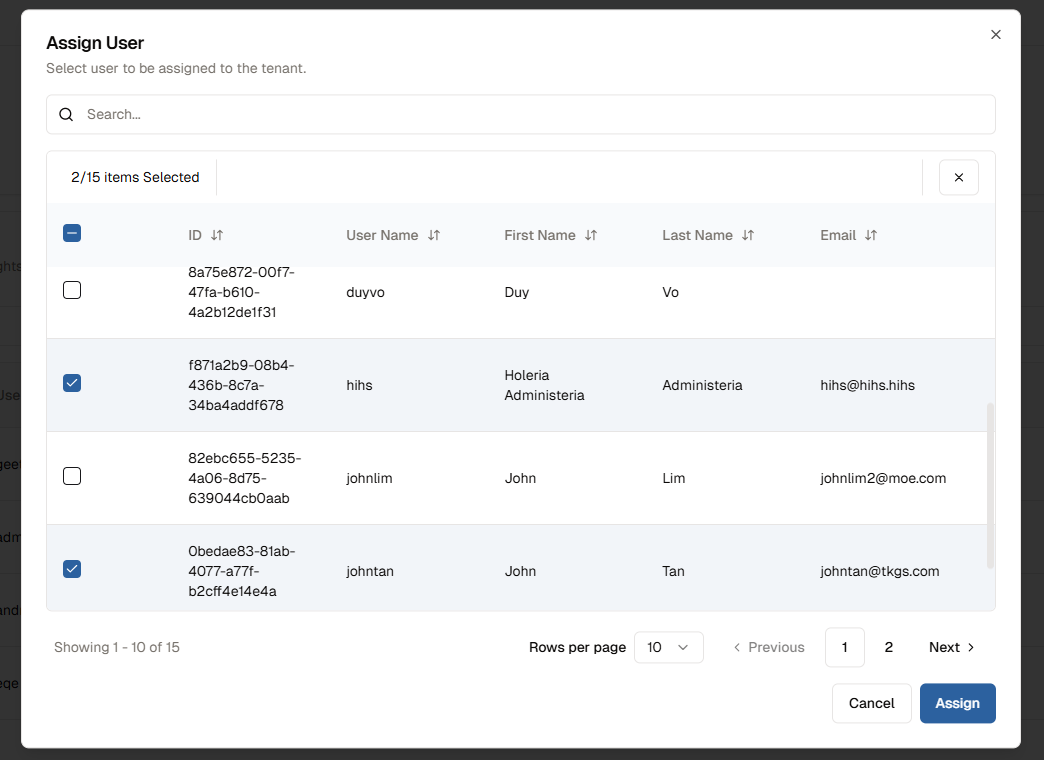
Assign Usersbutton to open .
- Check box the user accounts you want to add to tenant and click "Assign" button.
Password Policy
Password policies are managed through IAMS-Keycloak and define the rules that user passwords must follow.
How to Configure a Password Policy
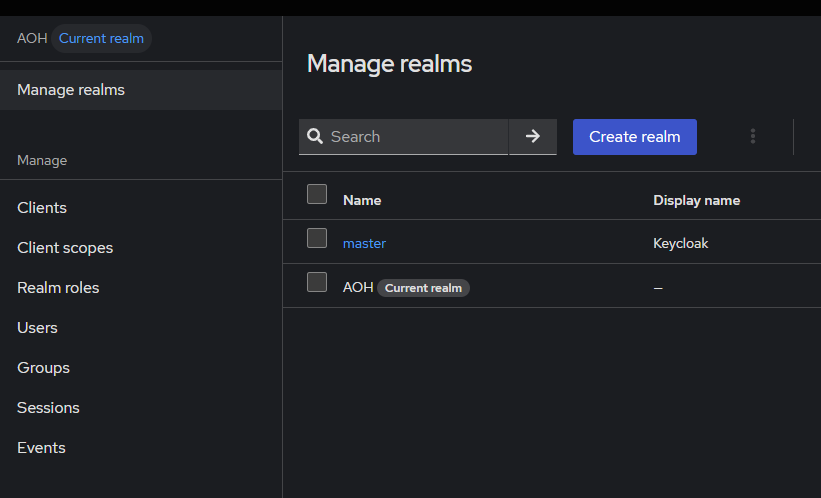
- Access the Keycloak Admin Console
Navigate to your Keycloak Admin Console and switch to the desired realm. In this example, we are using the AOH realm.
- Navigate to the Authentication Section
In the left-hand sidebar, click on Authentication, then go to the Policies tab.
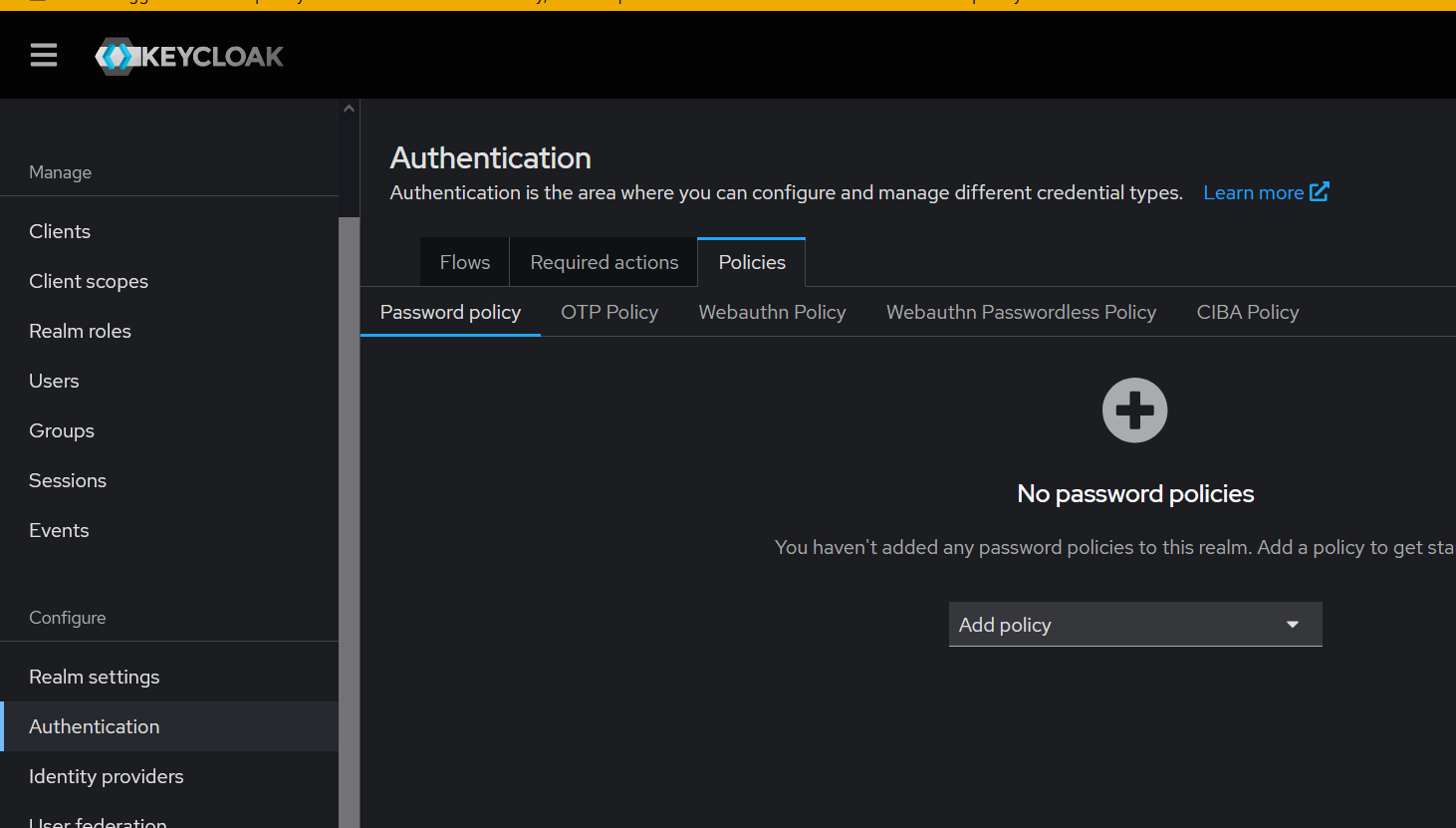
- Add or Modify Password Policies
Use the dropdown to add password policy rules such as:
- Minimum password length
- Required character types (uppercase, digits, etc.)
- Password history, expiration, etc.
After configuring the policies, click Save to apply the changes.
Soft Delete User Feature
Overview
The Soft Delete User feature allows disabling a user account without permanently removing their record from the database. Instead of deletion, the user is marked as deleted and access is revoked in Keycloak. This ensures that user data is preserved for auditing or recovery purposes.
When this feature is enabled:
- The user remains in the database.
- The user is disabled in Keycloak (login access revoked).
- A user attribute
isDeletedwith the valuetrueis added to their Keycloak profile.
You can restore the user at any time by re-enabling them and removing the isDeleted attribute.
Configuration
1. Enable Soft Delete
Set the environment variable in your service configuration:
ENABLED_SOFT_DELETE=true
If this flag is not set or is false, the system will permanently delete users instead of soft deleting them.
2. Keycloak Setup
Ensure the following configuration is applied in Keycloak:
- Access the Keycloak Admin Console
Navigate to your Keycloak Admin Console and switch to the desired realm. In this example, we are using the AOH realm.

- Navigate to the Realm settings Section
In the left-hand sidebar, click on Realm settings, then go to the General tab.
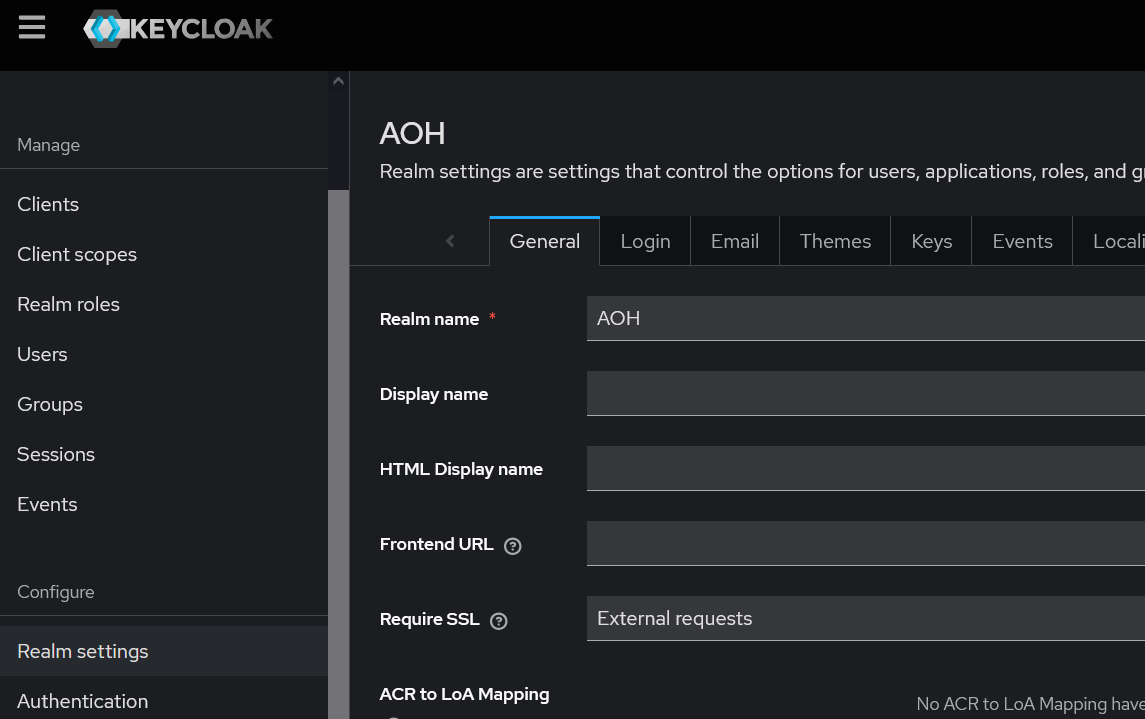
- Unmanaged Atrributes setting
Scroll down to the Unmanaged Attributes option and select Only administrators can write. Finally, click Save to confirm and apply the setting.
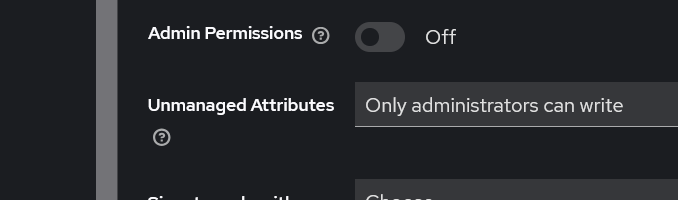
Restoring a Soft Deleted User
To restore a user who has been soft deleted:
- Go to the Keycloak Admin Console.
- Find the user in the Users list.
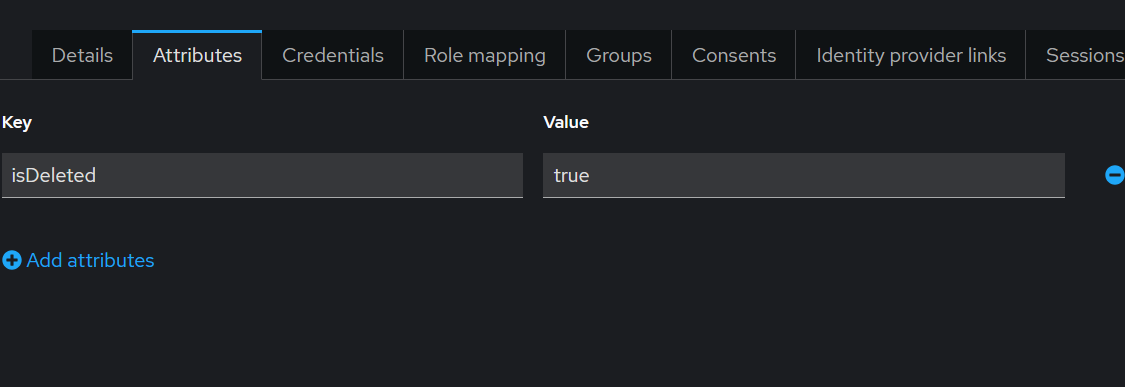
- In the User Details section, set the user status back to Enabled.
- In the Attributes tab, remove the
isDeletedattribute or set its value tofalse.
- Save changes.
The user will regain access to the system with their original data intact.